Ekoparty #15 Challenges Writeups
I know how it feels when a CTF or Challenge ends and you don't get the solution for a particular problem. So I decided to document how to solve the challenges I wrote for Ekoparty #15.
There were two challenges to solve for the Hardware Implant Challenge.
1. First Challenge
You can download the challenge file here.So what type of file uses logicdata extension. After a quick search of the file extension on Google, we get results pointing us to Saleae. We download the logic analyzer software from the Saleae web site and open the challenge file.
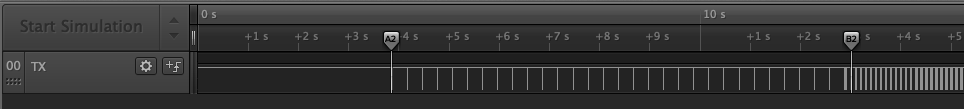
We have only one channel and it's named TX, so this could be UART.
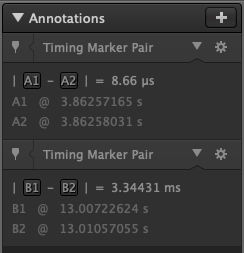
We also have two annotations. If we zoom in at the first annotation.
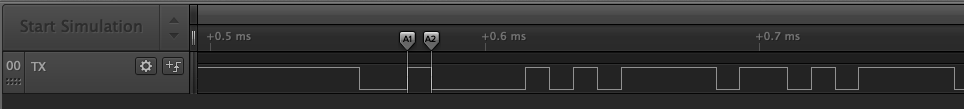
Looks like a measurement for 1 bit, based on this measure we could get the baud rate(aka bit rate).
1000000 ÷ 8.66 = 115473.441109
This number is very close to 115200, a known baud rate. We can setup the bit rate in the Async Serial analyzer.
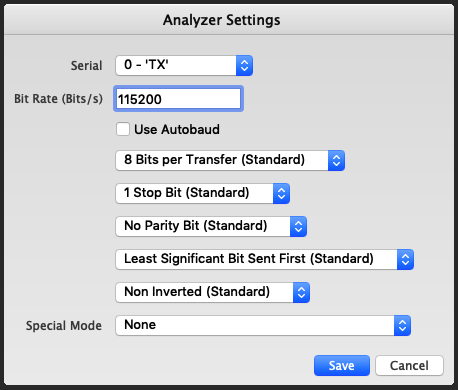
And we get the following:
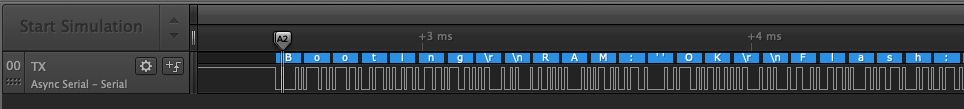
But when we get to the second notation, the analyzer is not able to analyze the signal.
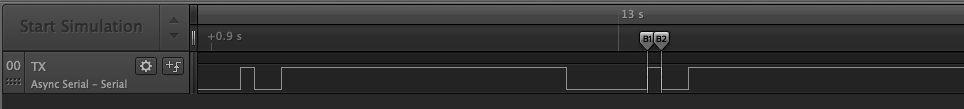
In the second anotation the measure is done is miliseconds instead of microseconds.
This number is very close to 300, apparently there were multiple baud rates in the same capture.
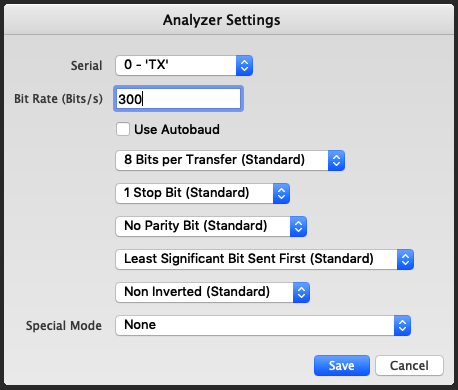
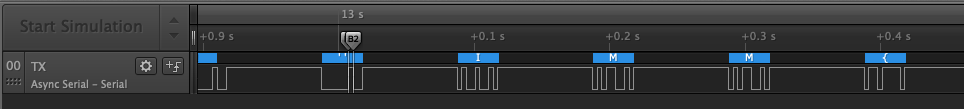 And finally we get the flag.
And finally we get the flag.
IMM{c1b82410259463fadbd84ddab4965b69}
2. Second Challenge
You can download the challenge file here. When we open this file we get the following:
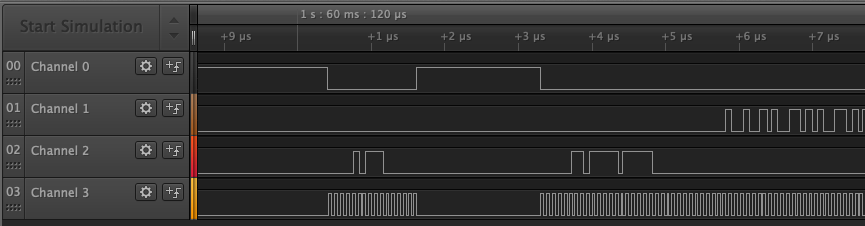
We could try different analyzers in this case, based on the signals we can assume we have a SLAVE SELECT(aka CHIP SELECT) on channel 0 and a CLOCK signal on channel 3. So this looks like SPI. But if we use SPI analyzer we don't really get something useful. During the presentation we mention that SPI are use on Flash Memory IC and if we search the web for SPI, flash and salea keywords we end up finding a SPI Flash analyzer.
Once we build the SPI Flash analyzer and restart the Saleae logic analyzer tool we just need to setup the analyzer plugin configuration.
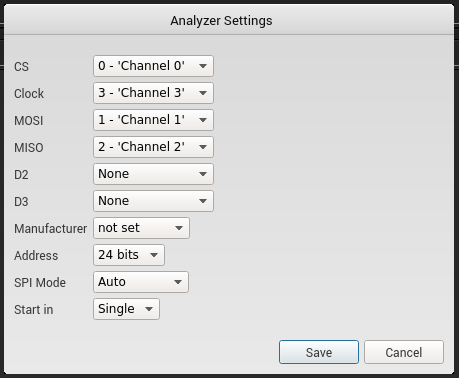
This will give us the flag.
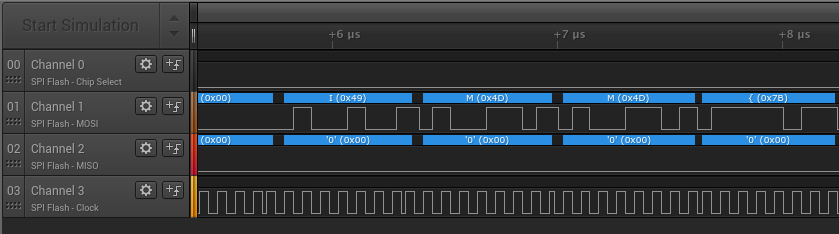
IMM{SPY_VS_SPY}